Hacking Your Passwords
While I was an instructor, the three areas I dabbled in were Routing & Switching (R&S), Voice over Internet Protocol (VoIP) and Security. I’ve posted a couple of times already on R&S and VoIP, but have been mulling over what is the right topic for Security. Posting on Security is a difficult task because people often assume too much or that tasks are easier than they actually are. As a CISSP, I’m also under an obligation not to undermine confidence in security:
“Promote and preserve public trust and confidence in information and systems.” -ISC2 Code of Ethics Guidance Associated with Cannon I
My thought process in justifying putting out a step by step on how to hack passwords on the internet is because posting this would 1) promote awareness of how easy this is to do and 2) to provide a recommendation on readily available tools that could increase security. The other reason is these methods are in no way earth shattering and readily available on youtube.
Next consideration is the relevance. I’ve heard people complain about security and ethical hacking courses because they teach how to hack “things people don’t use anymore”. I discovered in a technical manual for a very new (to the Marine Corps) equipment suite using the dreaded “enable password”, so I am sure we will see this out there.
Hacking a Weak Password: The Easy Way
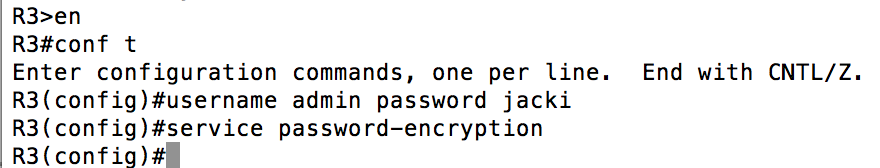
I’ve always taught my CCNA students that cracking Cisco Type 7 passwords (the type that would be generated if you used “enable password” and “service password-encryption”) is a simple google search away. While that did work every time, that is a bit of a cop-out. What happens if you did not have access to the internet? While I attended a CCIE bootcamp, taught by the excellent Marko Milivojevic, he showed us that IOS would happily hack them for us. Here is what that would look like:
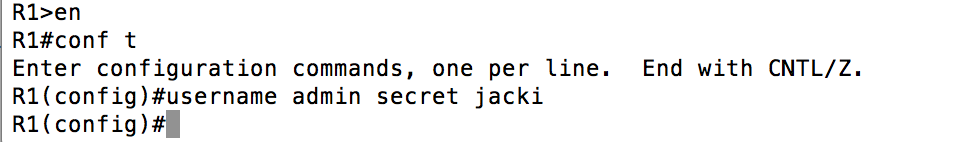
We start things off by creating a user by the name of “admin” with a password of “jacki”. Anyone who has been through a CCNA course knows you SHOULD be using “username ____ secret” which uses MD5 instead of Cisco Type 7, but more on that later.
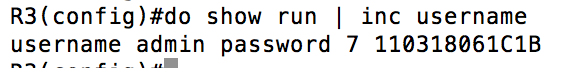 Next, we took a look at the running config to find out how this is stored. You need to copy the “7”, the space after it and all of the characters following the space.
Next, we took a look at the running config to find out how this is stored. You need to copy the “7”, the space after it and all of the characters following the space.
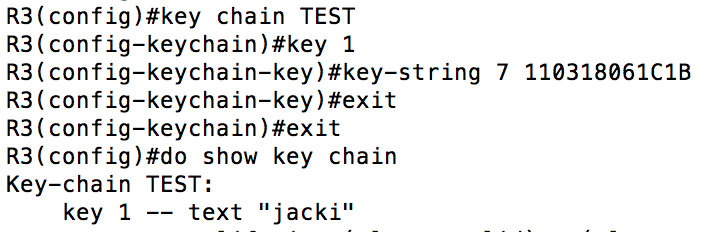
From there, all we need to do is create a key chain and paste our “encrypted” password in. **NOTE** if you leave off the “7” and the space this will not work. Leaving them off would create a new resultant instead of adding a previously computed one like we are trying to do.
Hacking a Weak Password: The Slightly Harder Way
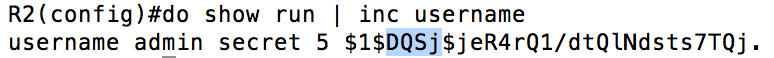
The method described above (which is my preferred method for deciphering Cisco Type 7) does not work for MD5 hashes. Cisco routers use a salted MD5 hash to store your “secret” passwords (such as “enable secret” or “username admin secret”). An MD5 hash alone would be vulnerable to a password attack using a rainbow table (taking all possible inputs and pre-generating MD5 hashes for them). The salt is randomness that is added in to protect against this. Here is what that looks like:
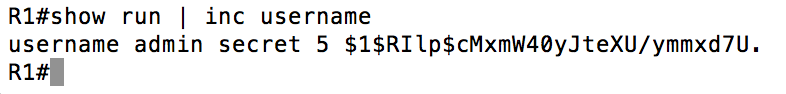
The highlighted portion is the salt in the above output. To show illustrate this, I will create the same username and password combination on another router:
From the above output you can see that different “randomness” as been added, and therefore the resulting hash is different. The strength of that randomness is the hacker is not supposed to know what it is. In this case, we see that all you need is access to the command line and privilege enough to execute a “show run” and you can easily find this out. Armed with this new info, how easy is it to crack the hash and find out the password? Let’s try it out.
First, if you do not already have Backtrack, head over to http://www.backtrack-linux.org/downloads/ to get the most recent version. This is a free open-source penetration testing suite. I’ve used this for both VM Workstation and VM Fusion and it has worked very well on both platforms. For those who have never used Backtrack before, launch the VM. After it has loaded, the default username is “root” and the default password is “toor”. Simply type “startx” and you will be in the GUI the following screenshots come from.
First we will create a user with an MD5 password.
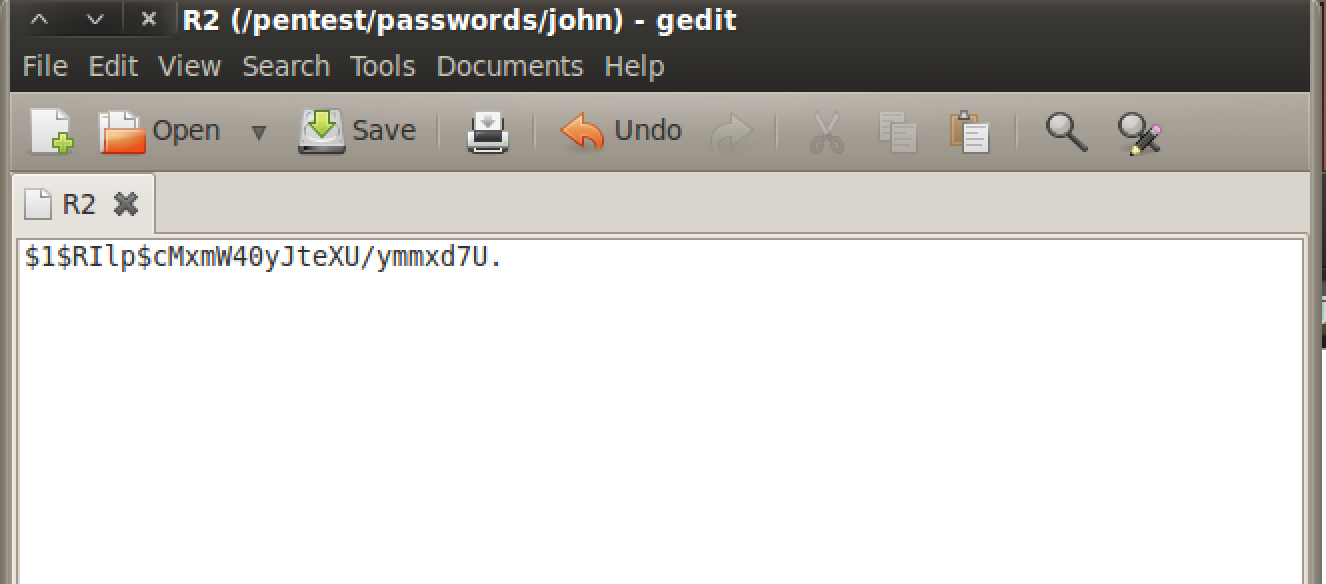
Then we will find out the salted MD5 hash. We will also copy the entire string (not including the 5 and the space).
Then we headed over to our BackTrack VM and pasted the string into a text document. For simplicity, I created this text document using the name R2 (it does not have to be named after the router you used) and I placed the document in the folder belonging to our cracking tool. To do this, simply navigate the file system to the desired folder, right click and chose “create document” -> “Empty File”. Paste the text we copied in the previous step to your newly created document. **NOTE** be careful about adding any spaces to your document as that technically changes the contents. Simply paste what you copied and save the file.
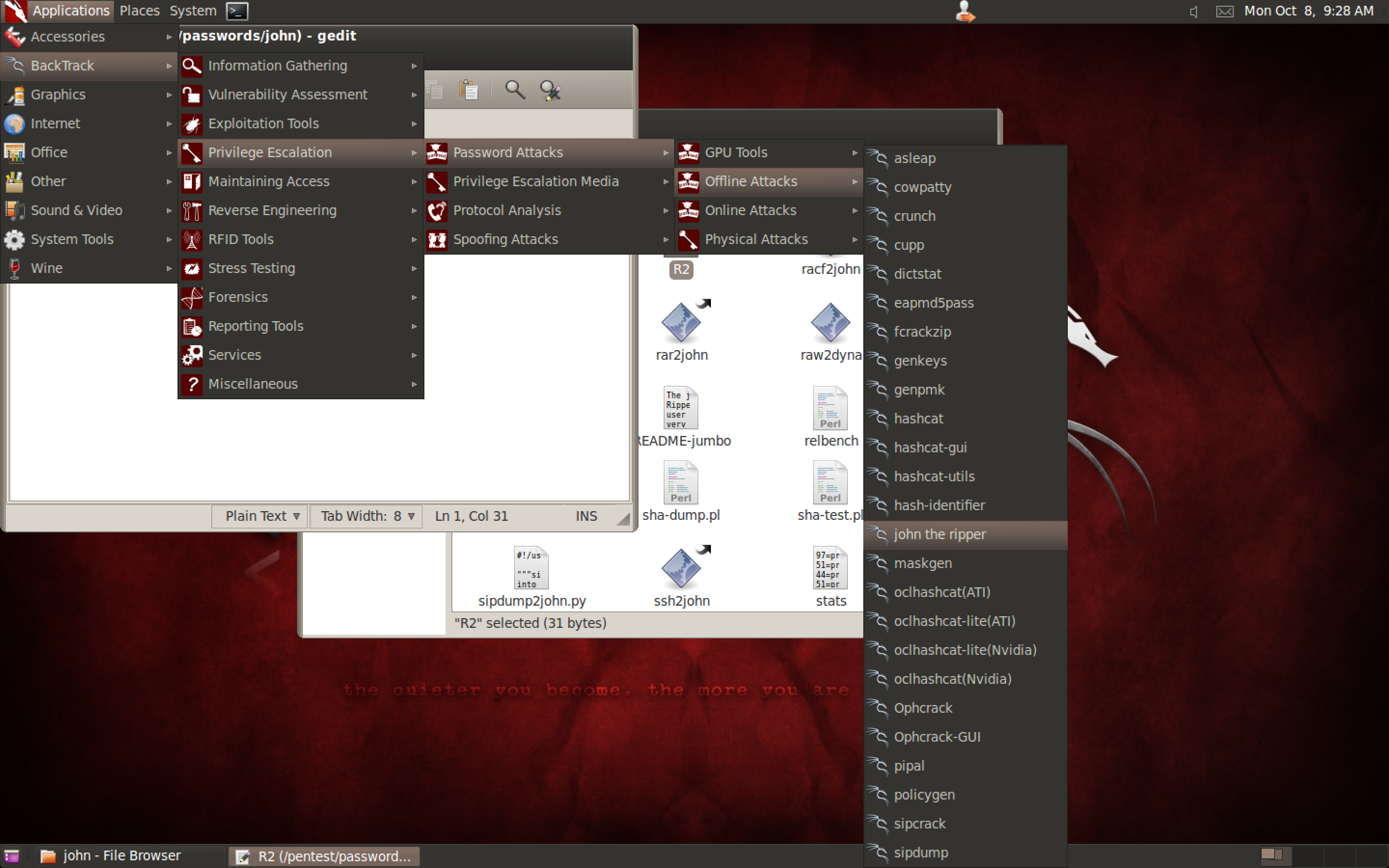
The tool we are going to use is “john the ripper”. You can reference the screenshot above for how to navigate there.
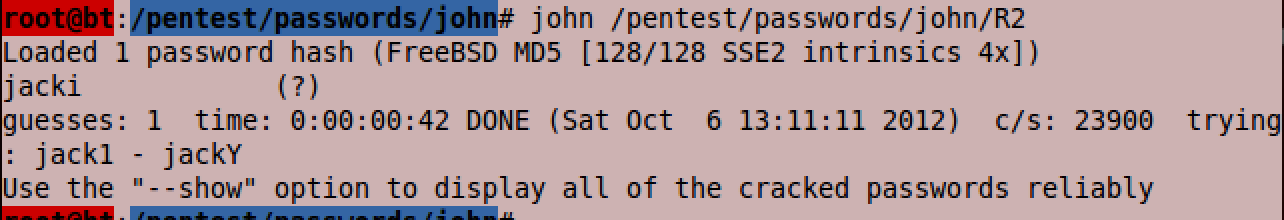
Clicking on “john the ripper” will take us to the command line. There is a lot more functionality to John than is shown here, but I wanted to illustrate that you don’t need to be a superhacker or very CLI savvy to be able to do this. Simply type “john” followed by the path to where your hash is stored, which in this case is “/pentest/passwords/john/R2”. This references the document we created in the previous step to find the hash. As you can see above, john was able to find out that our hash was created using the input “jacki”. This took 33 seconds.
“jacki” is not exactly what I would call a complex password and I would not expect john to be able to crack all passwords that quickly. The reason that john was able to crack “jacki” so quickly was because that password was in the wordlist that came with the program. Using a more complicated password that is not in the wordlist that comes with john, such as P@$$w0rd, is at a couple of hours (and counting) because it needs to be brute forced. Keep in mind though, I have BT running in a VM with only 1 virtual processor core and 768MB of RAM. You could crack that significantly faster by providing more resources to your virtual machine, or generating a better wordlist.
Although outside the scope of this post, it should be noted you can generate word lists with commonly used words and phrases (which you can gather using social engineering and automate using other tools in BT like “cupp”).
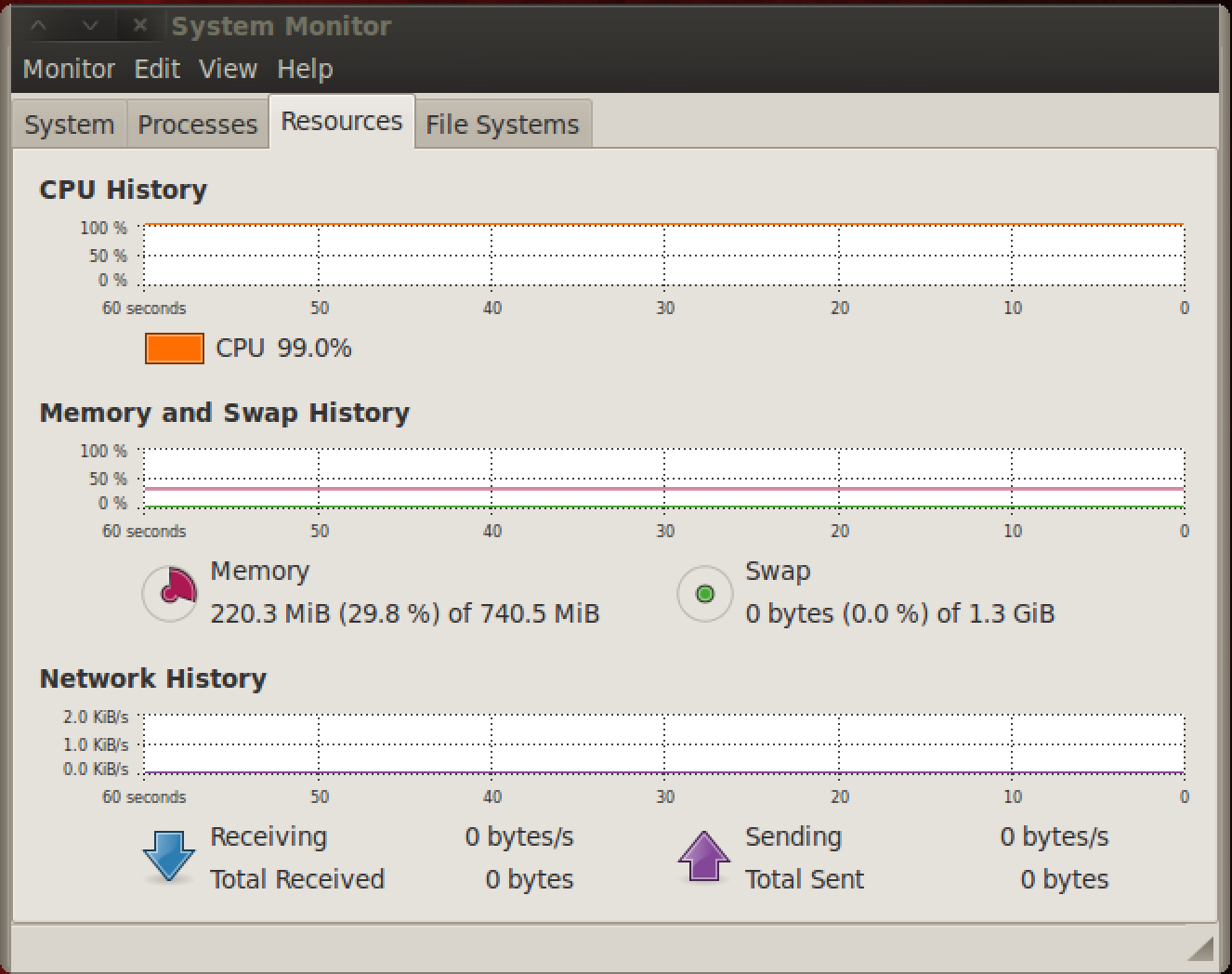
As you can see from the above screenshot, trying to brute force a password is a very resource intensive task.
What Now
Now that we know a couple of ways of cracking passwords, how can we improve our security posture? The first and most obvious is to not allow anyone access to our devices. Access to the command line needs to be restricted to only those who absolutely need it. This would include physical printouts of the command line. The next step is to not allow our configuration to be sent in plain-text across the network. We’ve done a good job about eliminating Telnet, notsomuch about eliminating TFTP. Using the password attacks used in this post, I would argue the end result of having someone intercept your configuration being transfered to a backup server via TFTP would be as bad as using Telnet. For whatever reason, TFTP has not been vilified the same way Telnet has. As Telnet has SSH as an alternative, TFTP has SCP. This post is running a bit long, so I’ll leave the step by step of these to a separate post.